In the world of IT, real news can easily get mixed with eye-catching headlines and promotional buzz. From a critical ransomware attack to tackling online abuse: filter out the noise with our selection of the top 3 tech news stories of the week.
Full podcast episode:
Join our community and find your next job or expert in IT
Ransomware attack: the new oil disrupting the old one
One of the most echoed statements about data is that it is the new oil. Regardless of whether you agree or not with this comparison ; you will surely find it ironic to see how much the decryption of data, this “new” oil, can end up affecting the old one.
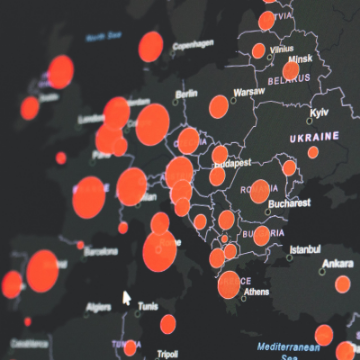
Last Friday, Colonial Pipeline, one of the largest oi pipeline operators in the United States, experienced a ransomware cyberattack that pushed it to shut down its IT systems. Linked to the DarkSide hacking group, the breach happened on the business side of the company’s IT infrastructure but affected its nationwide operations.
Although it is thought the motivations behind the attack were economic and not of sabotage, the incident reignites fears of the dangers hackers pose to a country’s critical infrastructure. Oil prices have gone up due to the supply disruption, with people all over the US piling up fuel reserves. The issue might not be fixed until the end of the week.
Self-taught robots
The idea of programming AI systems to teach themselves has been gaining major traction in recent years. Flexible software that is able to learn through experience makes a lot of sense. But our current capabilities in this regard might not be as far-reaching as we think.
A group of Amsterdam-based researchers built a simple robot and tried to make it learn how to move through trial and error. Made of independent units chained together into a train-like structure ; the robot used a series of inflating pumps to propel itself at a top speed of two millimetres per second.
Unfortunately, while the autonomous learning system managed to effectively move, maintain a stable pace and follow a circular track, the robot encountered a few real-world problems that threw all its calculations off. A good reminder of how easily a variable not accounted for can disrupt machine learning algorithms.
Tackling tech-enabled abuse
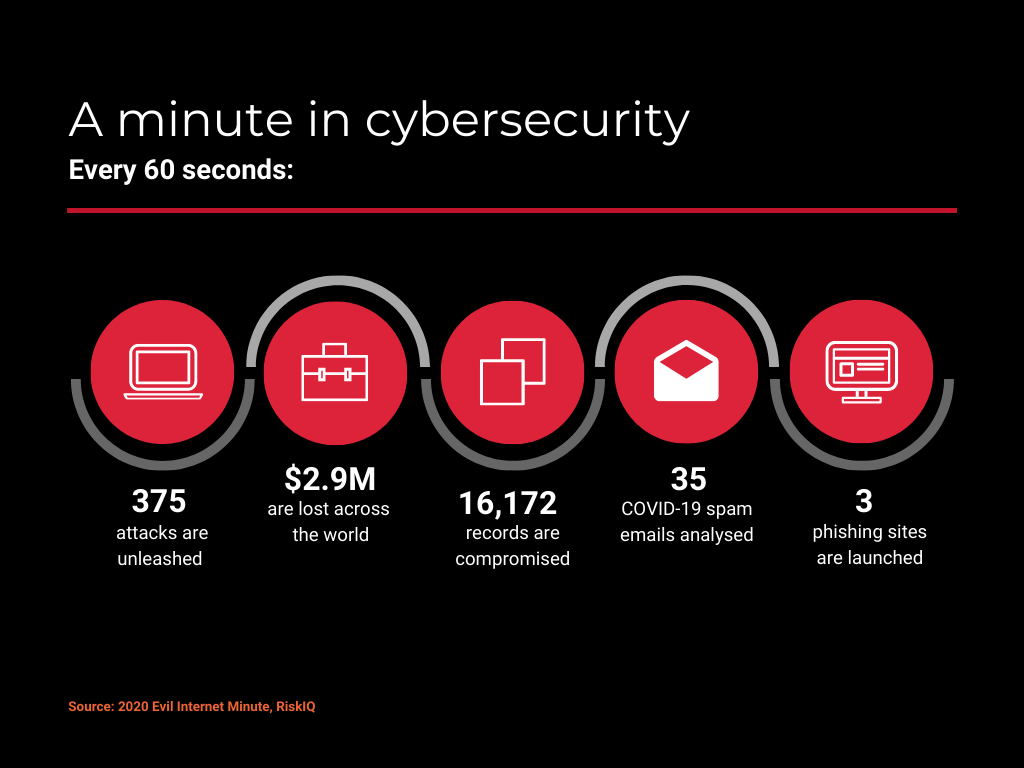
The tech boom caused by the pandemic has brought along some troubling side effects. An increase in online abuse is one of them. With the number of tech abuse cases requiring specialised assistance having grown by 97% over the last year.
All around the world, domestic abusers use both legitimate online tools and so-called stalkware to harass, control and monitor their partners. Suffice it to say, this kind of behaviour usually predates or accompanies other forms of abuse, from physical to psychological.
That’s why the Barclays-backed non-profit Refuge has launched a site to help abuse victims protect themselves from tech-enabled domestic abuse. RefugeTechSafety.org has been built with the help of survivors and provides educational and actionable resources in multiple languages.

Check out more of our interviews from our podcast episodes.