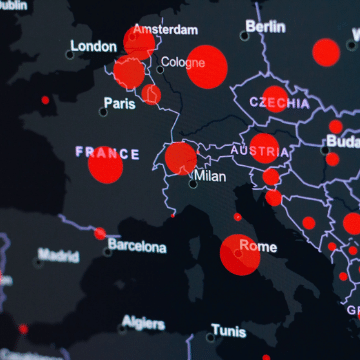
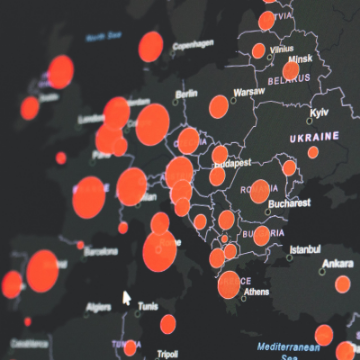
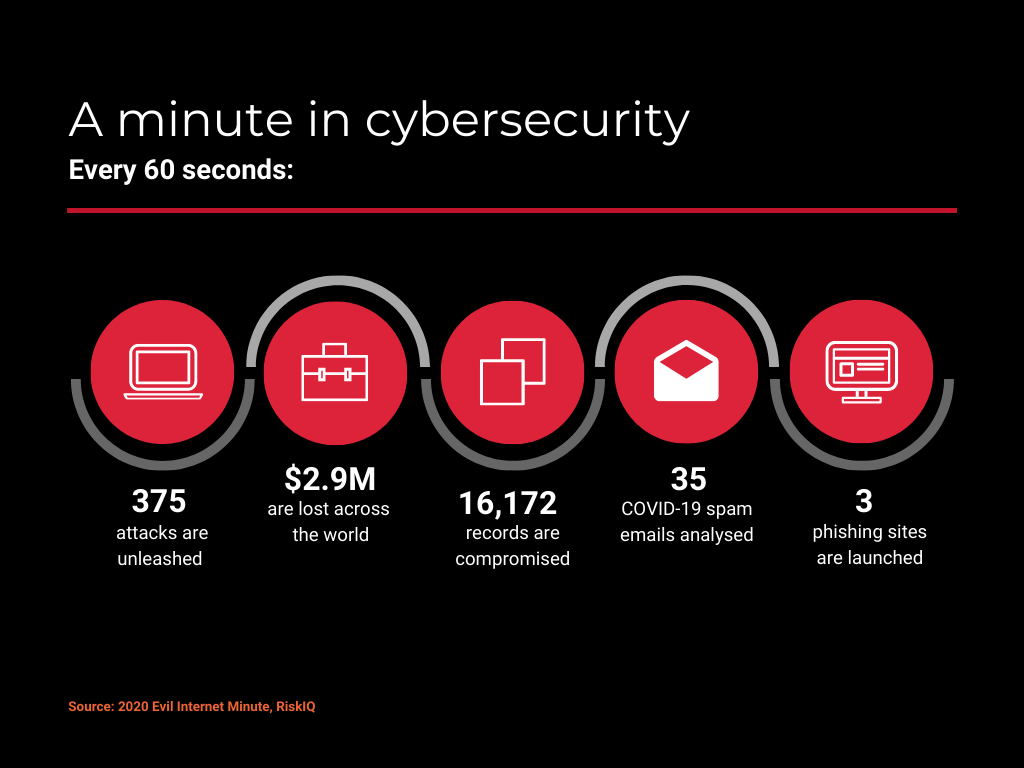
The increasing prevalence of IoT devices in homes worldwide raises cybersecurity concerns, emphasizing the need for proper usage to safeguard homes and families.
Common IoT Devices and Associated Cybersecurity Risks
IoT devices such as smartwatches, distance-measuring sneakers, home automation applications, and more, while enhancing convenience, also pose security risks if not used cautiously. These connected devices are susceptible to hacking, potentially compromising personal information and, in the case of geolocation-enabled devices, even indicating when homes are vacant.
Reports suggest that 2024 will see a surge in cybersecurity risk and threats to IoT devices. Therefore, awareness of these risks is crucial, prompting the need for users to secure their devices effectively.
The most common cybersecurity risk associated with IoT devices include personal data theft, knowledge of home habits, family geolocation access, fraudulent purchases, physical theft, identity theft, malware introduction, and illicit trading of personal data or images in underground markets.
Also read IoT Consultant Job Description
Recommendations for Cyber Protection
To mitigate these risks, Mindquest‘s experts recommend the following cybersecurity measures for IoT devices on a global scale:
Create Separate Networks: Establish dedicated networks for IoT devices using intelligent routers that create virtual networks. This prevents potential infections from spreading between computers and IoT devices.
Strong, Unique Passwords: Implement robust and distinct passwords for each IoT device, with regular password changes to enhance security.
Disable UPnP Protocol: Turn off Universal Plug and Play (UPnP) to hinder devices from easily discovering each other.
Regular Updates: Install the latest updates promptly, as they often include crucial security patches to address vulnerabilities.
Download from Official Sources: Obtain mobile apps exclusively from official markets to reduce the risk of downloading compromised applications.
Prioritize Security Settings: Review and prioritize the security settings of IoT devices over other functionalities to enhance overall protection.
Turn Off When Not in Use: Disable IoT devices when not in use to minimize the exposure to potential security threats.
User Training in Cybersecurity: Provide users with training and awareness programs on cybersecurity, especially for those utilizing IoT devices.
Cybersecurity Challenges of Smartwatches
As an illustrative example, we at Mindquest highlighted cybersecurity concerns specific to smartwatches:
Lack of Cybersecurity Standards: Smartwatches, like other IoT devices, face challenges due to the absence of specific cybersecurity standards.
Sensitive Information Collection: Smartwatches gather extensive personalized information, including GPS location, application notifications, biometric and health data, training information, and payment transactions, making them susceptible to data breaches.
Vulnerabilities in Design and Connectivity: The design and connectivity of smartwatches pose vulnerabilities that can be exploited by attackers. Weak user passwords and outdated systems further compromise security.
Limitations on Antivirus Software: Some smartwatches do not support antivirus software, leaving them exposed to potential threats.
Lack of Two-Factor Authentication: Absence of two-factor authentication in certain smartwatch designs increases vulnerability, especially in payment transactions.
Automatic Pairing Risks: Automatic pairing with other devices poses risks, necessitating the need to disable this function to prevent unintended connections with public or insecure Wi-Fi or Bluetooth networks.
Need advice on how to start or develop your freelance consulting business in tech or IT? Need to start a new permanent or freelance assignment? Join Mindquest and get support from our team of experts.