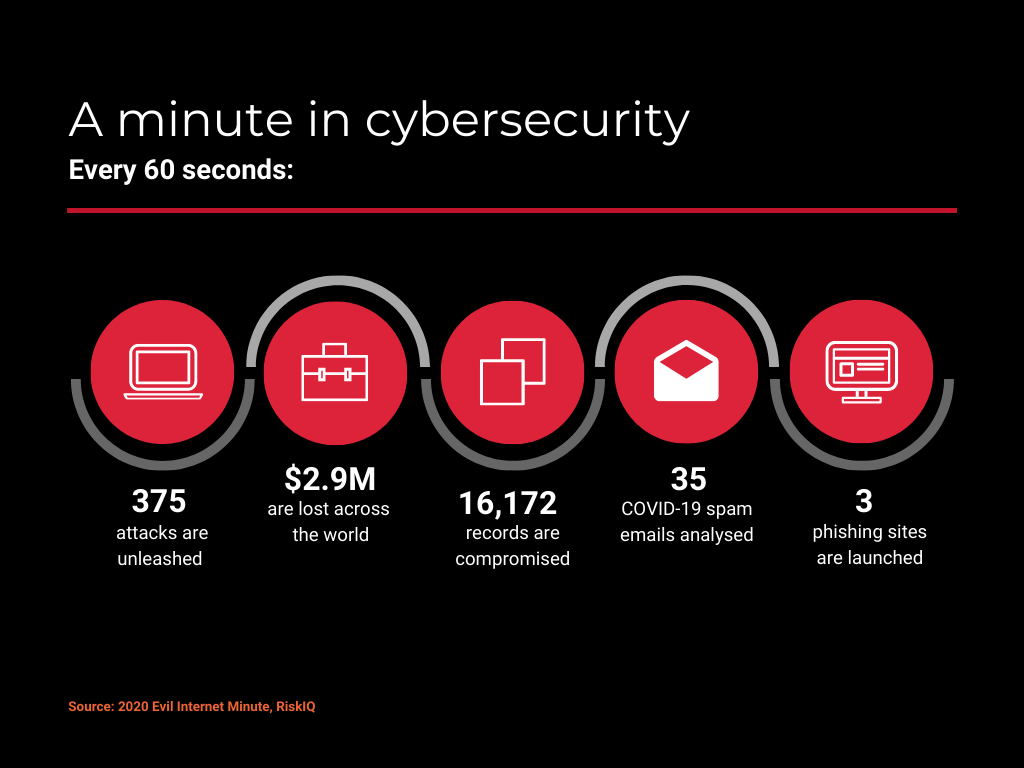
Cybersecurity is becoming increasingly complex, and it is no secret by now that the number of cyber threats companies face on a daily basis has increased dramatically as a result of the pandemic.
All in all, IT teams and their security experts are pulling extremely long hours to come up with better and more efficient ways of protecting their digital operations and data. As a consequence, that is accelerating digital transformation in the area.
According to IDG, most CIOs consider cybersecurity a top priority, with 65% of companies planning to increase their security budget this year. This increase in demand involves hiring extra staff to tackle cyber threats – a push that will surely accentuate the already severe drought of cybersecurity talent.
But all of this effort will not translate into long-lasting changes unless organisations institute a security-aware culture and take a more strategic and proactive approach to cyber protection. And that must necessarily start from the top.
Accountability
Nobody would be too surprised if a CEO was ousted after a major financial fiasco. Why would it be any different with cyber incidents?
A Centrify study from 2019 revealed that almost 40% of UK businesses had dismissed personnel for security-related incidents. You can bet not many of those employees were part of their company’s executive team.
Traditionally, security breaches have been considered a responsibility of technical teams and IT leaders, who often end up tracing the incident to a reckless employee who accessed sensitive information while sipping on a cup of coffee at a local café. Sure, human error and shadow IT are behind most cyber attacks, but, like with all systemic problems, a real cultural shift requires everyone’s involvement.
The truth is that technology is too integral to today’s businesses for companies to afford to have leadership that is not directly or at least ultimately responsible for it. Accountability not only ensures better performance; it drives innovation and promotes continuous improvement.
When an executive’s reputation and livelihood are at stake, they are more likely to push for deeper, company-wide initiatives to address potential cyber threats. They will, therefore, invest more resources in protection and become cybersecurity ambassadors within the organisation, setting into motion a series of changes spanning areas from HR to external contractors and business partners.
But to be accountable, business leaders first need to be knowledgeable.
Executive cybersecurity expertise
Recommending that executives be security-savvy is not to say that CEOs and other members of the board need to have deep technical knowledge of cybersecurity infrastructure and best practices, but they at least must be able to make informed decisions and factor cybersecurity into every key move they make.
One way to achieve such a boardroom environment is to hire executives with an IT background – a trend that is quickly gaining traction among the world’s top companies thanks to the inherent benefits that a strong technical foundation brings to business processes.
Another is to involve CIOs in the strategic decision-making process. IT leaders have acquired a bigger role since the start of the pandemic, growing closer to CEOs and becoming even more pivotal to business continuity than they were before. Companies should keep moving in this direction.
Newer IT-focused executive positions can also be created. Unfortunately, the figure of the Chief Information Security Officer (CISO) remains a rather rare occurrence in the c-suite. Although many companies have dedicated IT leaders in charge of cybersecurity, these are often confined to the IT department and do not get enough executive powers and visibility. Elevating CIOs within the organisation would certainly improve cybersecurity.
But not all solutions involve prioritizing executives with a technical background. Training is always an option. CEOs and their peers can learn to assess cyber threats and keep their company’s cyber resilience in mind when making business decisions. CIOs and their team have a key role to play in this training process, sharing their experience and actionable insights while delivering periodic security audits to inform the executive board.