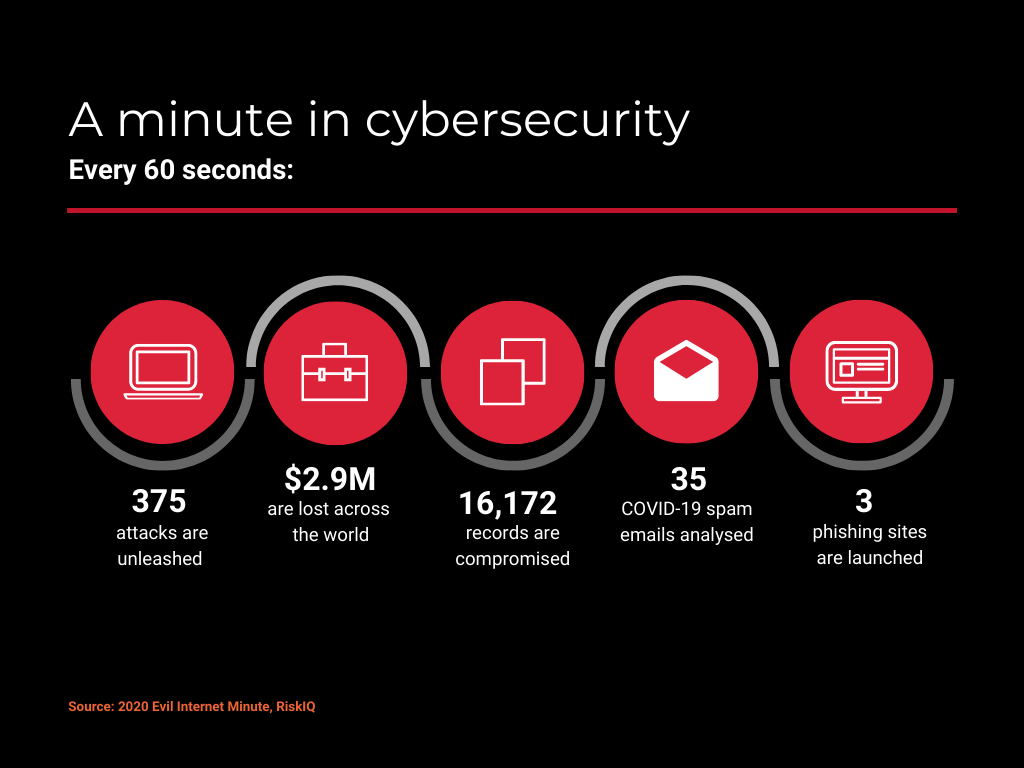
A surprising number of things can happen in a minute, especially when it comes to cyber threats and their consequences. Quick overview. The state of cybersecurity in 2020
Firstly, every 60 seconds, 375 attacks are unleashed upon the global community, costing the world economy $2.9 million. In other words, every single computer with an internet connection is targeted by malicious agents about 1.5 times per minute. A whooping 16,172 records are compromised.[1] Certainly not a promising picture if you are a business leader or oversee a company’s cybersecurity for a living.
As we celebrate cybersecurity awareness month to promote greater security and cyber hygiene, we would do well to keep in mind that every day should be cybersecurity awareness month. Therefore, we can all benefit from a deeper understanding of today’s most common threats and what we can do to protect our business systems from them.
Cybersecurity in 2020: the impact of the pandemic
The already complex world of enterprise security got further intricate with the advent of COVID-19. Also, the sudden shift to remote work has pushed company networks to the limit, opening a myriad of new potential points of entry for attackers to exploit. Additionally, the ensuing fear and confusion have given more leverage to attackers looking to deceive individual employees as a means to gain company-wide access. As they say: you are as strong as your weakest link. And hackers love that.
Social engineering, the act of tricking someone by using their natural tendencies and emotional reactions, has acquired a whole new dimension of sophistication and finesse. Phishing emails disguised as governmental safety announcements, fake HR memos encouraging you to get acquainted with the office’s new cafeteria policy. And that is just the start two per cent of all COVID-related websites created in recent months contain malicious code. A seemingly small number until you realise there are billions of COVID-19 pages out there.[2]
Remote work is here to stay, and so are the advanced techniques that cybercriminals use. In fact, they will only get more refined in the months to come.
A growing variety of cyber threats – Cybersecurity in 2020
In addition to the rising complexity of attacks, the sheer variety of techniques hackers use is a top concern for companies and cybersec professionals who are struggling to catch up with an ever-growing catalogue of threats. New forms of mobile malware alone, for instance, have grown 12% compared to last year. PowerShell-based malware, which leverages the Microsoft task automation and configuration management framework to carry out attacks without leaving any traces, grew by 1,902% over the same time period.[3]
Also discover our article & interview: Leadership Failure: The Real Human Element Behind Cyber Attacks
Targeting the cloud
Cloud has become the backbone of the modern enterprise, and hackers are targeting it accordingly. The rise in attacks is being particularly felt in those industries which depend the most on the cloud for productivity. For example, threats aimed at the transportation and logistics sector increased by 1,350% in the first quarter of the year. Education experienced a 1,114% rise in attacks, with governmental organisations, manufacturing and financial services following behind.[4]
The Top 10 Belgian Cloud Pros to Follow on Twitter
Most attacks are opportunistic in nature and involve the “spraying” of cloud accounts with stolen access credentials. The majority of access attempts came from either China, Iran or Russia. [5]
Ransomware-as-a-service
While phishing and trojans are still behind most cyber attacks, ransomware continues to surge and is perhaps the most feared malware of them all. Its capacity to cripple an entire company’s operations in a matter of minutes, together with how difficult it can be to prevent these attacks in the first place, surely keeps many security specialists and IT managers awake at night. Also, threat actors are becoming increasingly sophisticated.
What started as attacks by individual hackers or small rogue groups has now evolved into full-fledged criminal organisations that operate under a ransomware-as-a-service approach. Some even have “customer service” helplines to guide victims through the process of paying the ransom.
These hacker groups have greatly benefited from COVID-19, taking advantage of the increase in cloud usage and telework. Half of the world’s organisations were hit by ransomware last year, with most successful ransomware attacks involving public cloud data. Data was successfully encrypted in 73% of attacks.[6]
Additionally, attackers
are finding more and more weaknesses to exploit as remote workers and IT
engineers increasingly use Remote Desktop Protocol (RDP) to access internal
resources. The higher use of personal devices has also complicated the problem
of shadow IT, multiplying the potential points of access and making it more
challenging for security professionals to safeguard company networks.
Join our community and find your next job or expert in IT